We Define IT Consulting
Remote work has been embraced over the past two years, in no small part due to the impact of the pandemic. However, some of the impacts of remote work have made it clear to many businesses that its advantages shouldn’t be sacrificed once it is no longer necessary. Let’s review how businesses can improve by continuing the practices of remote work, even after the need for remote work has passed.
Windows 11 seems to be rapidly approaching, so now is the perfect time to discuss Windows upgrades and upcoming end-of-life scenarios, including Windows 8.1, which is slated to expire in 2023. You might be wondering if you have the hardware to handle this upgrade, and that’s a valid question, but what does the end-of-life scenario for Windows 8.1 really look like for your business? Let’s take a look.
Most modern businesses rely on wireless internet connectivity in their day-to-day processes. Of course, this means that their potential productivity is tied to the quality of their internet and its capability to serve the entire workforce. As a business grows it becomes more important that its Wi-Fi setup can support it. Let’s go over the process of properly scaling your network to your needs.
We throw the term “best practice” around a lot… enough that, without an appreciation for what the term actually means, it can start to sound like just another buzzword that the IT guy is using to sound more impressive. We assure you that this is not the case, and that the term “best practice” actually does mean something.
A virtual private network, or VPN, is a critical part of keeping your business safe while operations are taking place out of the office, but a discussion needs to be had about what a VPN can do and what a VPN cannot do. This is especially important to know for keeping your company safe, so without further ado, let’s dive in.
With more businesses moving in the direction of remote connections and mobile devices, it’s no surprise that wireless Internet is such a pain point for organizations. Sometimes it can be an exercise in frustration to connect to your office’s wireless network, and you might not really know what to do about it. Here are some ideas to try and increase your wireless network’s strength or signal.
Many states’ stay-at-home orders that are/were designed to mitigate the spread of the COVID-19 virus are now lapsing all over the U.S. As a result, business owners are re-opening their doors to a great deal of uncertainty. We have put together this guide to help the business owner understand that, even though you’ve finally been given the go-ahead, you have a responsibility to keep your staff and customers safe.
A new ransomware attack has surfaced, this time mostly targeting IT companies and their clients. The attack is specifically targeting the Kaseya platform. Kaseya is management software that many IT companies use to remotely manage and support technology. The attack in question attacked Kaseya’s supply chain through a vulnerability in its VSA software; this attack is notable because of how it targeted the supply chain, not only striking at the vendor’s clients—notably IT companies—but also their customers. Basically, this attack had a trickle-down effect that is causing widespread chaos for a massive number of businesses.
If you use almost any Apple products, you’ll want to check for and apply an update that will prevent your devices from being spied on. Apple has just issued an emergency software update for a critical vulnerability that was recently discovered.
The new updates were pushed out on Monday, September 13th, 2021, and include a major security fix for the Apple iPhone, Apple iPad, Apple Watch, and Apple Mac computers and laptops.
As time has passed, more focus has been put on balancing a user’s identity authentication in terms of its convenience versus its security. This is what has led to the development of solutions like Windows Hello, the biometrics-based system that Microsoft has introduced into the Windows operating system.
With businesses relying so much on technology to accomplish just about everything, IT undoubtedly has an important role to play. It makes sense that you would want your business’ IT to deliver as much value as possible. To accomplish this, we wanted to go over three IT-centric processes that are primed to help you do so.
Cybersecurity is a massively important consideration for today’s businesses, and as a result, managing it is often given a considerable amount of time. However, recent developments suggest that this time can potentially be reduced by the use of “self-healing” security software. We know that this sounds a little out there, but stay with us! We’ll explain.
While it only makes sense to assume that a cybercriminal would focus specifically on those targets that would bring them the greatest profit—in other words, larger businesses—the reality of modern cybercrime renders this assumption grossly outdated. Let’s examine how different developments in ransomware have made it possible for cybercriminals to be far less discerning in who they target.
Whether you refer to them as clients or customers, the people who act as patrons to your business are essential to its success and survival. This means that you need to keep them as happy as possible. While there are many aspects of maintaining a high level of customer service, we wanted to take a bit of time to examine how deploying the right technology can assist your business in doing just that.
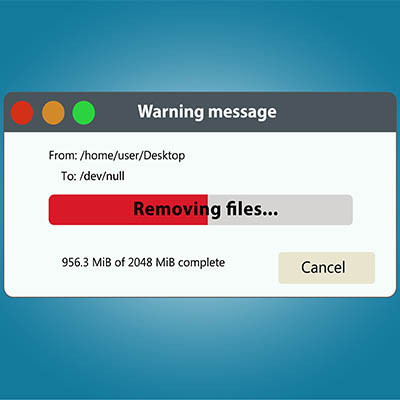
We’ve all been in a place where the storage on our computer fills up a little too quickly for our liking. While you could delete or store unused files in the cloud, there is another method that you can use to quickly free up a little extra space that you might not have realized is there. If you can delete temporary files, you might find that you suddenly have a lot more storage space to play around with on your computer.
Another ransomware threat is out and about, this time targeting unpatched and end-of-life products in SonicWall’s Secure Mobile Access (SMA) 100 series and Secure Remote Access (SRA) products. To make things worse, the threat is currently being used, so businesses utilizing these devices must take action now to limit how much damage this ransomware can do.
The process of implementing new technology for your business can be a tiresome, frustrating, and confusing process. This is especially the case when you implement a new technology solution only to find that it was absolutely not worth the effort. Let’s take a look at some of the reasons why your IT project deployment might not go according to plan, as well as how you can make sure this does not happen for your company.