We Define IT Consulting
In June of this year, publisher Chicken Soup for the Soul Entertainment, best known for its book series of the same name, filed for Chapter 7 and Chapter 11 bankruptcy and had many of its assets liquidated. One of these assets was the movie rental service Redbox and its eponymous scarlet rental kiosks, rendering the service defunct.
However, many kiosks remain standing outside businesses even now, which makes us wonder… what about all the data they collected while they were in use?
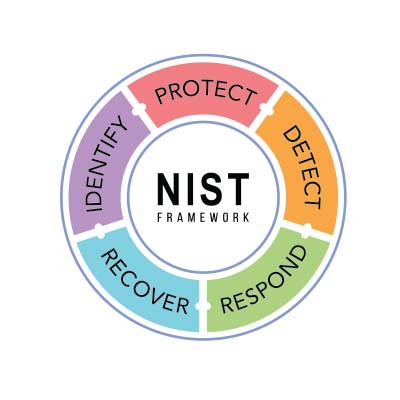
A well-structured framework is essential for establishing effective, consistent policies and strategies. This applies to many areas—including network security. Today, we’re diving into the National Institute of Standards and Technology (NIST) cybersecurity framework, which outlines steps to help safeguard your business.
Let’s have a little fun today. Today’s blog post is written in the format of a daytime soap opera. Please make sure you read all of the dialogue as if being whispered by extremely attractive television stars and starlets!
Life goes on in the small town of Oak Falls, deep woods surrounding the little hamlet nestled on the coast of Cape Seguridad. Let’s follow the lives of some of the residents, their lives Of Vice… and Vulnerability.
There’s never been a more dangerous time to run a business. Okay, maybe that’s not necessarily true, but hear me out. With digital technology taking on a greater importance for businesses than ever before, companies have to contend with countless threats—including the ever-popular phishing scams—regardless of their geographical location.
Modern wisdom states that if you’re not paying for a product, you’re the product.
For all the good the Internet is capable of doing, it is equally capable of being extremely harmful… especially when data is involved. Websites and social media platforms collect data from their users and track their movements across the Internet, sell it to advertisers, and more recently, use it to train AI.
Let’s go over what you can—and arguably should—do to limit these platforms' ability to do so.
It isn’t rare for people to subscribe to things and only stay subscribed because the cancellation process is so challenging and inconvenient. However, the Federal Trade Commission is looking to stop this, adopting a rule that eliminates the capability for businesses to put hurdles in front of cancellation processes.
Let me ask you something: would you trust a bank that locked its doors for the night but left all its cash in a big pile in the middle of the floor? Probably not—after all, if someone managed to get through the doors, nothing would stop them from helping themselves to the funds inside.
This is effectively how cybersecurity once worked, with the presumption that if someone had access to a network, they had permission to access any data on it. Fortunately, many businesses have made the switch to a better approach, known as zero-trust security.
Windows 11 takes a page out of Apple’s design playbook and features a taskbar that, instead of being off to the side, is smack in the middle of the toolbar. While some may like this change, others may not.
Fortunately for these others, a simple setting change can return the taskbar to its familiar place like on older versions of Windows.
Windows 11 features a robust desktop environment with a lot of neat tricks and customizations to work more effectively. Controlling your Windows desktop experience can enhance productivity and streamline the way you interact with your computer. In today’s blog, we give you four tips to help you customize and manage your Windows environment more efficiently.
“I don’t need to worry about cyberattacks… my business is too small to be of any interest.”
This brief rationalization is one of the most dangerous fallacies a modern business can make concerning cybersecurity, and shows a fundamental misunderstanding of how modern cyberthreats operate. If this has been your mindset, we urge you to read on so we can help set you on a more realistic path.
It’s natural for businesses to rely on their tools, like IT, to achieve success, but if you don’t take care of your systems, it could lead to downtime. You can bypass many of these challenges with the right approach to technology maintenance. We want to highlight some of the proactive methods you can use to keep downtime to a minimum.
Being a green business is certainly not a bad thing. Not only does it help boost your company's environmental friendliness, but it can often attract customers and clients who prioritize the environment. Less mentioned, however, is how being greener can actually give your business an advantage in the right circumstances.
Artificial intelligence is everywhere, and it is making data more valuable than ever. This is because AI platforms rely heavily on data to function effectively. Many platforms and services collect data from their users to fuel these algorithms. LinkedIn has recently been found to do this—by default—without properly informing its users or updating its terms of service.
“Toxic” is a buzzword that is often used nowadays, but when it is used to describe a business’ work environment, it needs to be treated with deadly seriousness.
If a workplace is a place people don’t like to be, many drawbacks will ultimately impact operations. Therefore, it is to your benefit to keep your business as positive a workplace as possible.
Let’s discuss how to tell if your company has a toxic workplace and, if so, how to resolve it.
File sharing is a big deal. When you try to send your friends a meme or share a video with them and it doesn’t send… that can be extremely frustrating. When it comes to business file sharing, miscommunication can cost quite a bit. Today, we will look at two concepts in small business file sharing and how they help a small business.
One of the many tasks undertaken by the United Nations is to protect human rights around the globe while also working to create more sustainable and climate-friendly development. As such, the UN has recently taken a healthy interest in the development of artificial intelligence, hoping to develop guidelines that allow us to get the most value out of AI without creating more significant problems.